Feature
Fingerprint Spoofing: Exploring Cybersecurity With Limited Technology
Connected Science Learning November–December 2022 (Volume 4, Issue 6)
By Patrick Burton, Kristin Cook, Rob Kelley, Jessica Ivy, and Kevin Thomas
As technology has become a more prominent part of our everyday lives in and outside of schools, cybersecurity knowledge and skills have become increasingly important. The National Science Foundation (NSF) describes cybersecurity as one of the defining issues of our time (NSF 2020). Recognizing the increasing need for supporting students’ understanding of cybersecurity, schools across the nation are weaving important cybersecurity concepts into their science, STEM, technology, or computer science classroom instruction. Through a summer STEM camp experience jointly funded by NSF and the National Security Agency, students learned about important cybersecurity principles. As cybersecurity is not always firmly rooted in the typical high school curriculum, this camp allowed for an inquiry-based and cross-curricular approach to “ignite, sustain, and increase awareness of K12 cybersecurity content and cybersecurity postsecondary and career opportunities” (GenCyber Program).
The following lesson was conducted during one of these STEM summer camps conducted with 25 high school students (grades 9–12) focused on cybersecurity, but the lesson could be implemented in a formal science or STEM classroom. This lesson also provides an example of exploring cybersecurity in connection with the crosscutting concept of influence of science, engineering, and technology on society and the natural world within the high school engineering design performance expectations (NGSS 2013). Also addressed is the International Society for Technology in Education (ISTE) Student Standard (2018) of Digital Citizen 1.2d: Students manage their personal data to maintain digital privacy and security and are aware of data-collection technology used to track their navigation online. Learning objectives include the following:
- Discuss the need for low-tech options when teaching cybersecurity principles.
- Create a prosthetic copy of fingerprint and use it to “trick” a touch ID scanner.
- Explain how and why a fingerprint scanner works and why this “spoofing” technique can be successful.
To explore one way in which “new technologies can have deep impacts on society and the environment, including some that were not anticipated (NGSS 2013),” this lesson teaches high school students to consider how their own cell phone technology can be hacked with a simple low-tech spoof. In the multiday lesson, students create a prosthetic copy of their fingerprint and use it to “trick” a touch ID scanner on a cell phone or tablet. Today, there are many high-tech ways to layer hardware security such as touch ID, facial recognition, location detection, iris and retinal scanning, and voice recognition to protect data on our personal devices; however, hackers can readily invade these security measures with relatively low-tech approaches. This fingerprint spoofing lab offers a context for teachers to discuss cybersecurity and how to protect our data from hackers.
The lesson involves each student casting a mold of their fingerprint in semi-dried hot glue, then filling the mold with a thin layer of Elmer’s glue. Next, students test their prosthetic fingerprint. This involves peeling the prosthetic print away from the mold, testing it in various ways, and attempting to unlock a cell phone (i.e., iPhone) or tablet device with Touch ID. This lesson can be completed in two 50-minute class periods.
Though this lesson is designed for students in grades 9–12, teachers should evaluate the level of background knowledge of their students to determine proper levels of scaffolding and pacing. Background knowledge includes an understanding that
- DNA codes for unique fingerprints,
- these unique features can be used to identify individuals, and
- the use of fingerprint analysis is particularly useful in the realm of forensic science.
This lesson is ideal for a summer camp, home learning environment, or after-school program where there may be limited access to technology; it can be conducted in a science or STEM classroom. Beyond the use of hot glue in the lesson, this low-tech lab is a safe, affordable way to consider the benefits and risks of biometric identity technology.
Background Information
Biometric recognition refers to the “use of distinctive anatomical and behavior characteristics or identifiers (e.g., fingerprints, face, iris, voice, hand geometry) for automatically recognizing a person (Maltoni et al. 2009, p. xi). Biometrics provide several advantages over traditional methods of user verification (e.g., numeric passcodes), including enhanced security. Biometrics are also more efficient and convenient than traditional methods of user verification (Maltoni et al. 2009).
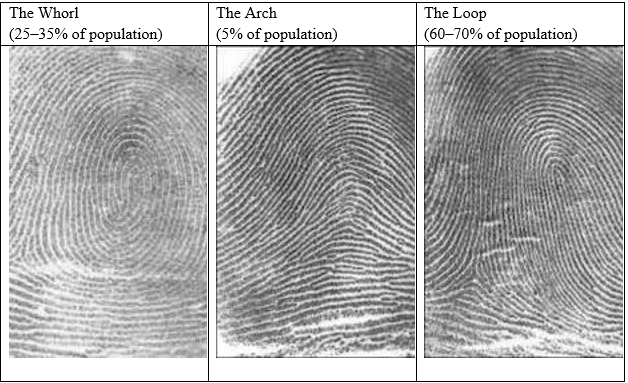
First introduced as an identifier over 100 years ago, human fingerprints are one of the oldest and most popular biometric traits in use, primarily due to their permanence and uniqueness (Roy, Memon, and Ross 2017). Decades of work have led to the classification of fingerprint minutiae, or the elements that make our fingerprints unique. Although there are over one hundred different characteristics that come into play, fingerprint analysis basically boils down to plotting the points where ridges end abruptly or fork into two branches. Combining that information with general fingerprint patterns—arches, loops, and whorls—creates a highly reliable way of identifying individuals (see Figure 1 for fingerprint types and percentage of population with each type). Fingerprint scanners incorporate all this data into templates, which are used whenever biometric authentication is required. This technological advancement has resulted in fingerprint sensors becoming a popular security feature for cell phones, tablets, and other technologies.
Fingerprint scanners work by capturing the three-dimensional pattern of ridges and valleys on a finger. The information is then processed by the device’s pattern analysis/matching software, which compares it to the list of registered fingerprints on file. A successful match means that an identity has been verified, thereby granting access. The method of capturing fingerprint data depends on the type of scanner being used. Devices like Apple’s iPhone and iPad use something called a capacitive sensor. Capacitive sensors use electricity (think of the way touchscreens work) to determine fingerprint patterns. As a finger rests on the touch-capacitive surface, the device measures the charge; ridges exhibit a change in capacitance at the device’s surface, while valleys produce practically no change at all. The sensor uses all this data to accurately map out prints.
Full human fingerprints are difficult to falsify. However, “the finger scanners on phones are so small that they read only partial fingerprints. When a user sets up fingerprint security on an Apple iPhone or a phone that runs Google’s Android software, the phone typically takes eight to 10 images of a finger to make it easier to make a match,” and since a finger putdown has to “match only one stored image to unlock the phone, the system is vulnerable to false matches” (Goel 2017). Recent research indicates that fingerprint scanning on smartphones can easily be fooled by fake fingerprints (Roy, Memon, and Ross 2017). With 95% of teenagers using mobile devices (Anderson and Jiang 2018), it is imperative that students understand that despite the advantages, fingerprint biometric systems are vulnerable to a variety of attacks (Uludag and Jain 2004), including a process called spoofing, which is the use of artificial fingerprints made using gelatin, Play-Doh, or silicone molds. These cloned fingerprints can be used by forgers for identity fraud (Uliyan, Sadeghi, and Jalab 2020). This lesson engages students in an authentic activity that exposes the risks to biometric authentication.
Fingerprint Spoofing Lesson and Lab
At the beginning of the lesson, students discuss questions (Appendix A) as a group (note: for formal educators, this can be completed by students as a prelab prior to coming to class). To assess prior knowledge, the teacher asks “What are some occupations other than forensic scientists and law enforcement who might use or store records of fingerprints?” Students read the background information above prior to the lab experience. Students list the three main patterns of fingerprint and draw three examples of minutiae that can be commonly seen in fingerprints, which helps assess their understanding of the content they read before the lab. The two-day lab experience is described below.
It is imperative to discuss the ethical considerations at hand, as students are essentially being taught how to hack into another group member’s personal device. It would be a good idea for students to sign a simple acknowledgement that indicates they understand this activity is for learning purposes only. For example, “I understand this activity is for learning purposes only. I will not use this information to unethically access other people’s devices without permission.”
Step 1: Creating a Prosthetic Fingerprint
Are fingerprint scanners really secure? In this lab, students work to create a prosthetic fingerprint to “trick” the touch ID on a device (such as an iPhone or iPad). This happens in two parts designed for 50-minute classes to allow for the finger mold and the prosthetic fingerprint to dry. Students first make the fingerprint mold/prosthetic fingerprint in class (see Figures 2 and 3 below, and Appendix B for lab details). Next, they complete the assigned background reading and answer the Part I questions. Once the mold has been cast, students learn more about what they are doing and why by reading Stanley Goodner’s (2021) article about finger scanners and how they work.


Step 2: Testing the Prosthetic Fingerprints
During step 2 of the lab, students attempt to unlock an iPad using the prosthetic fingerprints. As they perform these tests, students enter results into Table 1 (see Supplemental Resources). The control groups use real fingers to unlock the device (either the one stored on their phone or a real finger). The test groups use the prosthetic fingers. After they are done, students complete the postlab questions (see Appendix C) to showcase what they have learned.
Additional Connections
The Fingerprint Spoofing task allows students to integrate a variety of concepts. Students explore the science of fingerprints and intricacies of the technology as previously described. In addition, students can compare the observed versus expected occurrences of fingerprint patterns (Table 1) using mathematical models, such as a chi square test. Additional probability connections may include exploring the frequency with which the prosthetic prints are successful at unlocking the device. Additionally, an understanding of the materials used, such as the choice of hot glue and the requisite wait time, can integrate principles of thermodynamics and design. Process-related goals for this task can include opportunities for problem solving, application, communication, and reflection. A multi-discipline team could integrate opportunities for students to expand their writing on the ethics and cyber safety of fingerprint technology and the task itself.
Extension Activities
Teachers may choose to invest an additional 30–50 minutes before this laboratory activity to teach students about traditional, “by-hand” fingerprint analysis. Students can learn to identify common friction ridge patterns, assess their own fingerprints, and even learn to dust for fingerprints in the style of crime scene investigators. This requires additional materials, but there are a wealth of activities freely available on the internet to help guide this optional preparatory learning in the science classroom before applying technology and cybersecurity principles.
To extend discussion on the ethical considerations of this lab activity, teachers can relate the activity in the fingerprint spoofing lab to cybersecurity ethics by reading Hayes’s (2019) article on ethics of biometric identity. Questions you may want to consider include:
- What are some ethical questions or concerns that arise from this activity?
- Detailed biometric information has been gathered by large institutions (e.g., the military or police). Are people justified to feel a loss of privacy or personal dignity?
- How will our personal information be safeguarded by these institutions?
Many newer phones and tablets no longer have fingerprint scanners because companies have switched to using better technologies that secure the devices. However, cheap fingerprint scanners can be purchased for around $25 from companies such as SparkFun or AdaFruit. They can be integrated into Raspberry Pi computers or Arduino boards for small do-it-yourself systems. Building these could be integrated into an engineering class or used in any course.
Additionally, teachers may want to extend learning by engaging students in discussion about newer technologies being used in the most recent iterations of phones and tablets. An additional laboratory/engineering lesson could be incorporated that centers on the question of how facial recognition software could possibly be “spoofed” in a similar way to the fingerprint lab protocol. Students can brainstorm ideas, write up plans or blueprints, and even design prototypes.
Differentiated Learning Opportunities
Students can work at varying paces throughout the lesson, with additional time provided as needed. Teachers may also need to offer individualized assistance, as necessary, throughout lab and discussion sessions. Teachers may also consider having students work in pairs or small groups for a number of reasons. If using devices owned by the students, not all members of the group may have access to their own device with fingerprint analysis. Students with physical constraints or differences may also be unable to use fingerprint analysis touchpads, though they can participate in the lesson in other ways such as by assisting other students with their molds and testing.
Program Evaluation
The outcome of this hands-on STEM experience was positive in the summer camp setting, with participants successfully “spoofing” prints and fooling devices. Even more valuable than this tangible success was students’ recognition of the potential crosscutting applications of this activity. Teachers wanted the students to understand the importance of cybersecurity and how hackers use biotricks to unlock personal information.
In addition to the pre- and postlab questions, teachers asked students (through an exit slip) (1) what they learned or what surprised them about the learning experience and (2) what they learned about cybersecurity. Student reflections following the performance task supported the premise that cybersecurity concepts can be targeted across the science curriculum and can be taught without the latest technological advances in the classroom. One student commented that cybersecurity “principles could be broken down in a simpler way depending on the subject,” indicating that this often-intimidating content can be made more accessible by spreading it across the curriculum. Another student noted that “high-tech topics can be taught in low-tech environments,” while another said that “even with added security my phone could still be hacked—with glue of all things!” This commentary anecdotally supports the teaching team’s belief that this activity was a success.
One unexpected complication was that the Elmer’s glue prints did take longer than anticipated to dry. While it is likely possible to conduct the full lesson in a 90-minute block class, teachers should plan adequate drying time for the glue. Participants should also be cautioned to use a minimal amount of glue, which will aid in the drying process. In retrospect, it also may have been useful to begin with a demonstration of forming and casting a fingerprint mold for the class. This would serve to not only give students a visual for the appropriate amount of Elmer’s glue to use, but also allow them to see how long the hot glue should cool before safely pressing the finger into it.
Conclusion
Because cybersecurity is a growing area of interest in both education and future careers, science and STEM teachers should consider incorporating related topics into their own classrooms. The NGSS prompts educators to explore how technology impacts society both in terms of benefit and unintended consequences. Significant technological advances like fingerprint scanning and biometrics offer the benefit of securing our personal information and providing peace of mind, but also carry great risk. Fingerprint biometrics may be unique to each person, but using this methodology to identify people comes with a cost that once the information is compromised, it will be compromised forever.
As teachers seek to provide experiences for students to complement the goals of the NGSS, it is important to focus on cross-curricular integration of science, technology, engineering, mathematics, and the arts. Through hands-on laboratory activities and real-world applications, teachers can provide students with authentic experiences that not only support classroom learning but also provide practical knowledge to help prepare them for technological advances that are sure to continue in the years ahead.
Acknowledgments
This work was jointly supported by the National Security Administration and the National Science Foundation GenCyber Program under Grant Number H98230-19-3-1-017. Any opinions, findings, and conclusions or recommendations expressed in this material are those of the authors and do not necessarily reflect the views of the National Science Foundation.
Special thanks to Victoria Hale of Mercy Academy in Louisville, Kentucky, for her assistance in the development of classroom materials and testing of the lab protocol with her students.
Patrick Burton is a STEM teacher at Mercy Academy in Louisville, Kentucky. Kristin Cook (kcook@bellarmine.edu) is a science educator, Rob Kelley is a computer scientist, Jessica Ivy is a mathematics educator, and Kevin Thomas is a technology educator, all at Bellarmine University in Louisville, Kentucky.
Teaching Resources
Note: Websites and Sources below may change depending on what is available and accessible.
Goodner, S. (August, 2021). What are finger scanners and how do they work? Fingerprint scanners for smartphones, tablets, laptops and more. LifeWire: Tech for Humans. https://www.lifewire.com/understanding-finger-scanners-4150464
Hayes, N. (March, 2019)). Ethics and biometric identity. Security InfoWatch.com. https://www.securityinfowatch.com/access-identity/biometrics/article/21072152/ethics-and-biometric-identity
Saplakoglu, Y. (April, 2018). Why dead fingers (usually) can't unlock a phone. LiveScience. https://www.livescience.com/62393-dead-fingerprint-unlock-phone.html
Uliyan, D.M., S. Sadeghi, and H.A. Jalab. 2020. Anti-spoofing method for fingerprint recognition using patch based deep learning machine. Engineering Science and Technology, an International Journal 23 (2): 264–273.
citation: Burton, P., K. Cook, R. Kelley, J. Ivy, and K. Thomas. 2022. Fingerprint spoofing: Exploring cybersecurity with limited technology. Connected Science Learning 4 (6). https://www.nsta.org/connected-science-learning/connected-science-learning-november-december-2022/fingerprint-spoofing
Instructional Materials Labs Lesson Plans STEM High School Informal Education